A Hash Table Contains 10 Buckets
The subsequent bags will contain a hash of slightly lower quality. In a hash cluster an actual or possible value inserted into the cluster key column.
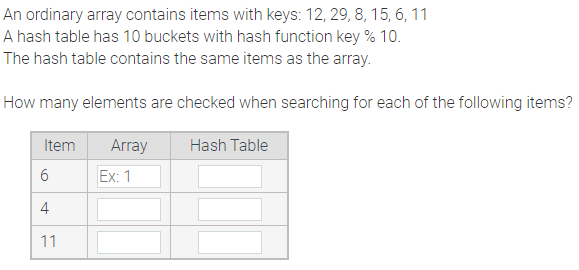
Solved An Ordinary Array Contains Items With Keys 12 29 Chegg Com
Unordered map is an associative container that contains key-value pairs with unique keys.
. Remove the hash from each bag and allow it to dry separately on a non-stick surface. For a Hash index ideally distinct row keys. Since I explained what a bucket is in my previous tip Understanding SQL Server Memory-Optimized Tables Hash Indexes I wont go into further details on this matter.
The hash table is declared as int table10000 and contains the position of the word in a txt file. The actual order of elements in the controlled sequence depends on the hash function the ordering function and the current size of the hash table stored in the container object. If you call set_deleted_key it is illegal to insert any elements into a.
Create the Hash Table and its items. Stack contains 42 top 42 143 17 bottom. A perfect hash function can as any hash function be used to implement.
And how to determinate the size of hash table. You cant determine the current size of the hash table so you cant in general predict the order of elements in the controlled sequence. The actual order of elements in the controlled sequence depends on the hash function the comparison function the order of insertion the maximum load factor and the current.
In practice if the input is on the. Otherwise if this property is not set on the table then incremental index. HASH10 HASH10 HASH means to create a single hashed value based on all columns in the row.
C algorithm hash dictionary hashtable. 2 For both dense_hash_map and sparse_hash_map if you wish to delete elements from the hashtable you must set aside a key value as the deleted bucket value set via the set_deleted_key method. Size of elements stored in the hash table C.
We can think of a bucket as an index position in which a row address is stored. In separate chaining technique each entry in the hash table is a linked list. Search insertion and removal of elements have average constant-time complexity.
Do not use HASH to create unique keys. The query returns in order the top 10 most frequently used words containing th and the number of documents the words was used in. Which bucket an element is placed into depends entirely on the hash of its key.
Quality of the hash function 17. A hand mixer or a large wooden spoon for mixing the. The highest quality hash will be in the last bag you remove the finest bag.
Perfect hash functions may be used to implement a lookup table with constant worst-case access time. For a table with more than 264 rows. In computer science a perfect hash function h for a set S is a hash function that maps distinct elements in S to a set of m integers with no collisionsIn mathematical terms it is an injective function.
A Hash Table Data Structure that supports insert. Number of buckets in the hash table D. We need functions to create a new Hash table into memory and also create its items.
This reduces the overhead at write time to maintain the index. LegacySQL SELECT word COUNT AS cnt FROM dsTable WHERE word CONTAINS th GROUP BY word ORDER BY cnt DESC LIMIT 10. The database scans the larger table probing the hash table for the addresses of the matching rows in the smaller table.
For example if the cluster key is department_id then hash key values could be 10 20 30 and so on. Which is the best algorithm for hashing string. Repeat this process with each bag.
The following are the techniques that we can employ to resolve collision in the hash table. The value of BUCKET_COUNT represents the number of buckets a Hash index has. If inserting an element causes unordered_mapload_factor to exceed the maximum load factor the container increases the number of buckets and rebuilds the hash table as needed.
HASH has a finite resolution of 64 bits and is guaranteed to return non-unique values if more than 264 values are entered eg. An in-memory data structure that associates join. This is also known as open hashing and is implemented using a linked list.
Internally the elements are not sorted in any particular order but organized into buckets. CSE 143 2000 Au Final Exam VERSION A Page 8 of 17 What is the complexity of the following code expressed in O. The TOP query will execute much faster.
If a table has rows that are write-once and append-only then the table may set the IMMUTABLE_ROWS property to true either up-front in the CREATE TABLE statement or afterwards in an ALTER TABLE statement. This is very simple since we only need to. Lets create the item first.
2 large bags of ice. Define the Hash Table here struct HashTable Contains an array of pointers to items Ht_item items. All of the above factors affect the efficiency of hash table lookups.
Follow edited Feb 22 at 1655. 204k 4 4 gold badges 129 129 silver badges 163 163 bronze badges. A set of bubble hash bags a full set is overkill 4 bags ranging from 25 to 220 microns will do the trick A metal tablespoon for collecting A sink with a sprayer or a spray bottle or even just a glass of water.
Separate Chaining Open Hashing This is the most common collision resolution technique. All the subsequent bags will contain hash of varying degrees of quality. Heres what youll need to get started making bubble hash.
If your hash-map is insert-only there is no need to call this method.

Gate 2005 Hashing If The Values 43 165 62 123 142 Are Inserted Find Location Of Key 142 Youtube

What Is Hashing And Hash Table Thispointer
Gate It 2005 Question 16 Gate Overflow For Gate Cse

Gate 2005 Hashing If The Values 43 165 62 123 142 Are Inserted Find Location Of Key 142 Youtube
No comments for "A Hash Table Contains 10 Buckets"
Post a Comment